Top 15 Hacking Tools Every Hacker Should Have in Collection

What comes to mind when you hear the word “hacker?” For most people, it is probably a picture of some nefarious person in a dark room stealing your sensitive information. While all hackers do not have righteous intentions, the hacking landscape has changed completely in the last several years.
Companies and organizations now employ hackers to conduct what are called penetration tests to see where their digital data may be vulnerable. Any hacker worth their salt already has some tricks up their sleeve, but there are some useful new tools out there, too. Check out our list of the top 15 tools every hacker needs to maximize their success.
 This is infamous as one of the most frequently used and effective password crackers on the market. Conversely, it is also known as one of the best tools to test the strength of your own passwords, as well as the strength and safety of your operating system, even remotely.
This is infamous as one of the most frequently used and effective password crackers on the market. Conversely, it is also known as one of the best tools to test the strength of your own passwords, as well as the strength and safety of your operating system, even remotely.
One of the most appealing features of John the Ripper is that it has been built with the ability to auto-detect any type of encryption used in any password. It changes its algorithm according to the password it is testing, making it the most intelligent and intuitive password cracking technology available.
If that weren’t enough, John the Ripper is also available across almost all platforms, including Android, Mac, Linux, and Windows.
John the Ripper is dubbed as an “ethical hacking tool,” but unabashedly uses brute force to reach its goal of deciphering algorithms and passwords, such as:
- Hash LM (Lan Manager), the system used in Windows NT / 2000 / XP / 2003
- DES, MD5, Blowfish
- MD4, LDAP, MySQL (using third-party modules)
- Kerberos AFS
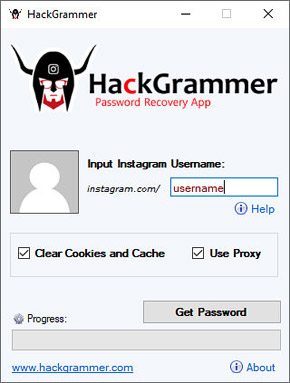 It was developed with the prolific Instagrammer in mind. If you have been locked out of your Instagram account, HackGrammer is here to help you not only recover your password, but your photos, as well. The authors of the app make it clear, however, that any liability or responsibility lies in the hands of the user, and they are not responsible for users putting their app to nefarious use, such as hacking another user’s Instagram account.
It was developed with the prolific Instagrammer in mind. If you have been locked out of your Instagram account, HackGrammer is here to help you not only recover your password, but your photos, as well. The authors of the app make it clear, however, that any liability or responsibility lies in the hands of the user, and they are not responsible for users putting their app to nefarious use, such as hacking another user’s Instagram account.
The bulk of the magic with HackGrammer takes place in its code:
- Customized add-on that spoofs brute-force hacking whose goal is to access Instagram’s login page to circumvent them not allowing your IP address to access your account after too many failed log in attempts
- Uses its own VPN servers to assign virtual IP addresses
- Constant upgrades to allow access and the latest technology
 This packet sniffer and network interceptor is used specifically for LAN networks. It supports both passive and active scans and even caters to encrypted scans, such as HTTPS and SSH.
This packet sniffer and network interceptor is used specifically for LAN networks. It supports both passive and active scans and even caters to encrypted scans, such as HTTPS and SSH.
Additional proficiencies include network manipulation via established connections, which is a fantastic way to detect and test man-in-the-middle attacks. It also includes host and network analysis, like the OS fingerprint feature, for example.
The most appealing features of this tool include:
- DNS Hijacking
- Included protocol supports are Imap, Telnet, Smb, FTP, MySQL, NFS, SNMP, LDAP, and HTTP
- SSH and HTTPS encryption-based protocols
- Filters based on IP source and destination, Mac and ARP addresses
- Data injection into established connections
- Extensible with plugins
- Sniffs remote traffic over GRE tunnel
- Able to kill established LAN connections
- Active and passive protocol analysis
- Determines OS name and version
- Plasma RAT
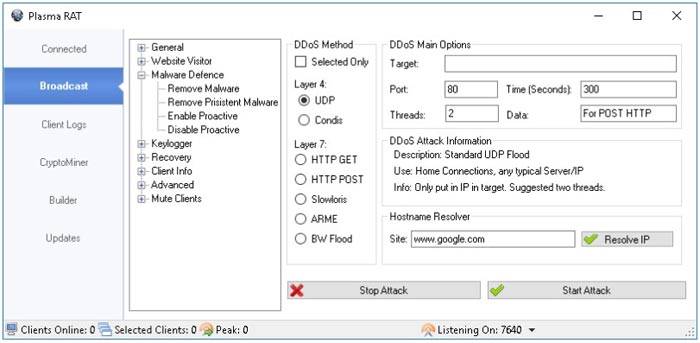
Remote administration trojans, or RATS, have been a popular choice for hackers for a while now. Plasma RAT specifically is a tool in which a client server application is housed. It allows its users to remotely access other people’s computers and to wrench control from the owners’ connection.
Plasma RAT is also unique as it allows users to establish control over many computers all at once, as well as allowing you to mine crypto currency.
Some of the most appealing features of Plasma RAT include:
- Password Recovery
- Task Manager
- Script Execution
- Keylogger
- Crypto Currency Miner
- Remote WebCam
- Chat between Client/Server
- NanoCore RAT
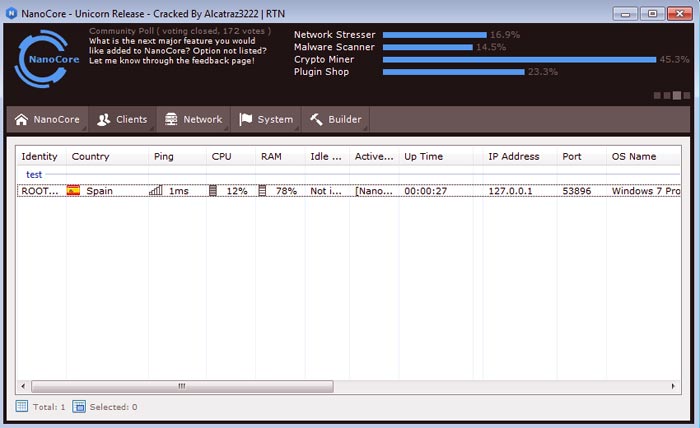
First created in 2013, NanoCore RAT made its first appearance on the Dark Web; that scary, nameless place wherein only a select few are welcome and comfortable. NanoCore is categorized as a “modular” RAT, meaning that the user can implant and activate additional NanoCore modules, which can expand performance and functionality.
NanoCore is a great option for amateur threat actors, as its functionalities are meant to be extremely automated and intuitive. Those who are just starting out or who lack the required skills to impact real damage prefer NanoCore for their hacking needs.
The most desirable features of NanoCore include:
- Base plugins to expand functionality
- Additional plugins available for more specifically malicious intents
- User friendly dashboard and interface
- Available live feed shows progress and damage in real time
If you are looking for an open source cyber-security platform that allows infosec specialists to implement varying penetration testing options to detect and remedy software vulnerabilities, Metasploit may just be the tool for you. It also doubles as an exploit module platform.
Experts may have heard of the Metasploit Framework, which was written by Ruby and is the most famous result of Metasploit. This framework allows you to test, develop, and execute these exploits with great ease. The tools offered in this framework allow users to:
- Execute remote attacks
- Run security vulnerability scans
- Evade detection systems
- Enumerate networks and hosts
To offer some variety, there are three different versions of Metasploit available:
- Community: used by small companies and infosec students.
- Framework: the best for app developers and security researchers.
- Pro: ideal for penetration testing and IT security teams.
Metasploit is currently available on Linux, Mac OS X, and Windows.
Network Mapper, or NMap, is an open, free source security option favored by infosec specialists to audit and manage network and operating system security for remote and local hosts.
Launched in 1997, NMap is one of the oldest security tools on the market, it is consistently updated and improved to keep it competitive with the newer models. It is also still widely viewed as one of the most effective tools available, with a reputation for being fast and for always having positive results without the necessity of a security inquiry.
Interested parties can expect the following features when using NMap:
- Find vulnerabilities inside any network
- Detect open ports on remote hosts
- Launch massive DNS queries against domains and subdomains
- Network mapping and enumeration
- Audit device security
NMap is available on Solaris, Linux, OpenBSD, Mac OS X, and Windows.
AirCrack-ng is considered a reliable Wi-Fi security suite that specializes in corporate security and home investigations. It offers robust support for WPA-PSK and 802.11 WEP networks and operates by detecting and capturing network packets. After the networks are captured, it analyzes them to infiltrate Wi-Fi access.
AirCrack-ng pleases security specialists that consider themselves old-school with its terminal based interface in addition to some more modern features, such as:
- Launches PTW, WEP and Fragmentation attacks
- Active community (forums and IRC channels)
- Cracks quickly
Integration with 3rd party tools - Support for Linux, Mac and Windows Wi-Fi detection
- Extensive documentation (wiki, manpages)
- Multiple Wi-Fi card support
- Supports WPA Migration Mode
If you are looking for a free, open sourced software that allows users to capture and analyze data traffic, Wireshark is the tool for you. Thanks in large part to its unique sniffing tech, Wireshark is hailed for its ability to detect security breaches on any imaginable network, as well as its unwavering ability to solve most general networking errors.
While Wireshark “sniffs” the network, specialists intercept and interpret results in a format that is actually readable for humans. This feature makes it much easier to pin down potential issues and vulnerabilities.
The main selling points of Wireshark are:
- Protocol decryption includes but not limited to, Kerberos, IPsec, SSL/TLS, SNMPv3, WPA/WPA2, and WEP
- Rich VoIP analysis
- Packet browser
- Saves analysis for offline inspection
- Powerful GUI
- Inspects and decompresses gzip files
- Supported ports and network devices: Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI
- Exports results to XML, PostScript, CSV, or plain text
Wireshark can be your best friend on Mac OS X, NetBSD, OpenBDS, FreeBSD, Linux, and Windows.
Another remote administration trojan, DarkComet RAT specializes in allowing users to control a system with a graphical user interface, or GUI. This RAT has many features that allows the user to capture information, such a screen grabs, password stealing, and key logging.
DarkComet has been discontinued as of August 2018, thanks to its correlation with the conflict in Syria in 2014, but before its demise, it was a favored option for hackers the world over. Some of its features included:
- Keylogger
- Webcam Capture
- Sound Capture
- Url Download
- Active Ports
- Browse Page
- Remote Desktop
- Poweroff
- Shutdown
- Wi-Fi Access Points
- Restart
- Logoff
- Network Shares
- Server Socks5
- LAN Computers
- Net Gateway
- IP Scanner
- Redirect IP/Port
For those not entirely sold on Metasploit, Canvas is a fantastic alternative, offering more than 800 exploits intended to test remote networks.
Canvas also gives you the bonus of having the option to write your own exploits, as well as allowing you to use its infamous shellcode generator. On top of that, it integrates an NMap alternative, called ScanRand, which specializes in host discovery and port scanning on mid-to-large scale networks.
Some of the more desirable features of Canvas are:
- Escalates privileges to gain administrator access
- Downloads passwords
- Targets selected geographic regions
- Remote network exploitation
- Targets different kind of systems
- Takes screenshots of remote systems
- Modifies files inside the system
Canvas can currently be enjoyed on Linux, Windows (with Python and PyGKT), and Mac OS X (with PyGKT).
Written in Python, Wapiti is a free, open sourced vulnerability scanner that is based on command lines. It may not be the most popular tool on the market, but it is very effective at finding deficiencies on many varying web applications.
By implementing Wapiti, you may find:
- Server-side request forgery
- XXE injections
- SQL injections
- XSS attacks
- XPath injections
- CRLF injections
Bonus features include:
- Sets custom user-agent and HTTP headers
- Runs in verbose mode
- Timeout configuration for large scans
- Ability to pause and resume scans.
- URL extractor from javascript
- Highlights vulnerabilities found inside the terminal
- Bypasses SSL certificate verification
- Generates reports and export into HTML, XML, JSON and TXT
- Excludes URLs during an attack
- Activates and deactivates multiple attack modules
- Removes parameters from certain URLs
Ethical hackers tend to gravitate toward IronWasp, a free, multi-platform and open source tool that is perfect for experts looking to audit their own web applications and servers.
However, the most desirable feature about IronWasp is that you don’t need to be a specialist to use it properly. It is GUI-based, which makes for an inherently user-friendly experience. This is a fantastic stepping stone for those just beginning their foray into ethical hacking.
Some of IronWasp’s main selling points include:
- Supported platforms: Windows, Linux with Wine, and MacOS using CrossOver
- Powerful GUI-based interface
- Full Python and Ruby support for its scripting engine
- False positive and negative management
- Web scan sequence recording
- Exports results into HTML and RTF file format
- Can be extended by using modules written in C#, Ruby, and Python
- 25+ different web vulnerabilities
Part of the Kali Linux Distribution, Nikto is another fan favorite. Fedora, another Linux distribution, comes ready made with Nikto already built into its software storehouses.
This security program scans web servers while proctoring several different tests against a targeted remote host. It has a very simple and clean command line interface, which makes it a user-friendly option.
Nikto’s main draws are:
- Integration with Metasploit Framework
- Detects default installation files on any OS
- Intrusion detection system evasion with LibWhisker
- Detects outdated software applications.
- Exports results into plain text, CSV or HTML files
- Runs XSS vulnerability tests
- Launches dictionary-based brute force attacks
Maltego is a superb tool that can be used for data reconnaissance and gathering intel while performing a pointed, first analyses of your chosen target.
For instance, Maltego is incredibly useful in determining and correlating relationships that exist between social network profiles, companies, phone numbers, people, names, email addresses, and organizations.
The most enticing Maltego features are:
- Can copy and paste information
- GUI-based interface
- Generates entity lists
- Analyzes up to 10.000 entities per graph
- Exports graphs to GraphML
- Extended correlation capabilities
- Correlated data graphics generator
- Data sharing in real time
With the number of viable, reliable options out there today, there is something available for hackers of all types and skill sets.